Hire Cybersecurity & Information Security Talent
Cyber threats are evolving, and so is your need for top-tier security talent. From ethical hackers to cloud security architects, BridgeView helps you build a security-first workforce, ensuring compliance, risk mitigation, and business continuity.


Cybersecurity & Information Security Tech Roles We Fill
- ● Security Engineer
● Network Security
● Cloud Security Engineer
- ● Security Architect
- ● SOC Analyst
● GRC Analyst
● IAM Analyst
- ● Threat Intelligence Analyst
● Vulnerability Management Analyst
● Penetration Tester
● Incident Response Analyst
A Hiring Approach That Works For You

Contract/Contract-to-hire
Access on-demand, flexible support for technical positions.
Statement of work (SOW)
Build committed project-based teams with defined timelines.

Direct hire
Find the right FTE long-term skill- and cultural fit for your team.

How You Get Top Talent, Guaranteed
1. Discover & Analyze
We start by collaborating with client leadership to define the ideal candidate profile. Our team methodically analyzes requirements, develops targeted screening questions, and customizes outreach strategies to ensure the best fit.


2. Source & Select
With a national reach, AI-powered tools, and our proprietary DragonHire platform, we identify top talent efficiently. Our 60,000-candidate database ensures fast, precise matching.


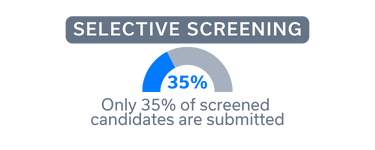
3. Screen & Test
A two-step screening process ensures candidates align with job requirements through functional, technical, and cultural assessments. Online tests, video screenings, and Q&A evaluations verify technical expertise.



4. Verify & Validate
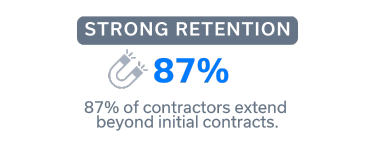
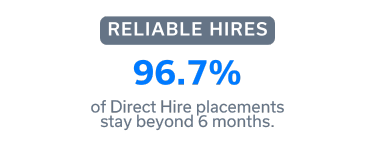
We conduct background checks, employment verification, and reference checks to confirm every candidate’s credibility. Our W2 contractors receive competitive benefits to enhance retention.

FAQs
Are you ready to build your Cybersecurity & Information Security team?









